 What the Enterprise Mobility Suite solution of Microsoft unique makes, is the Office suite which is available for iOS and Android. (and later this year on Windows 10 Mobile) One of the apps of the suite is the Outlook app. This app on iOS and Android can be managed via the Mobile Application Management policies in Microsoft Intune to control data leakage. When you want to prevent data leakage you may want to force the users to use the Outlook app instead of the native mail and calendar apps on iOS and Android.
What the Enterprise Mobility Suite solution of Microsoft unique makes, is the Office suite which is available for iOS and Android. (and later this year on Windows 10 Mobile) One of the apps of the suite is the Outlook app. This app on iOS and Android can be managed via the Mobile Application Management policies in Microsoft Intune to control data leakage. When you want to prevent data leakage you may want to force the users to use the Outlook app instead of the native mail and calendar apps on iOS and Android.
This can be done, let’s see how.
In this scenario we want to control access to the email in Office 365 and force the usage of the managed Outlook App. Default behavior is that when you enroll the device, the device will have access to Exchange Online, so both the Outlook app as the native app will be able to synchronize with Exchange online. We don’t want to have that.
What we need is the following;
- Setup Microsoft Intune Service to Service Connector for Hosted Exchange
- Compliance Policies
- Conditional Access for Exchange Online Policy
- Exchange Access Rules
Microsoft Intune Service to Service Connector for Hosted Exchange
Using the Microsoft Intune Service to Service Connector for Hosted Exchange allows you to define and use the mobile device access rules of Exchange Online. With the Exchange Access Rules you are able to configure access to Exchange ActiveSync based on device family and device model.
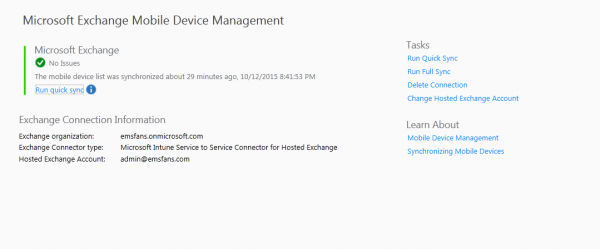
Setting up the service to service connector for hosted exchange is easy. Just logon with a user that has Global Admin permissions in Office 365 and the same tenant. If logged on with such account just click Set Up Service to Service Connector and click OK in the Admin > Mobil Device Management > Microsoft Exchange > Microsoft Exchange node in the Intune Admin console.
Compliance Policies
When using Conditional Access for Exchange online you are able to check if the device is compliant before allowing access to Exchange Online. Settings that can be checked are for instance if a password is set, if password complexity is set, but also is a device is encrypted or if the device is jailbroken or rooted.
If a device is not compliant the user needs to configure it so that it is compliant again to get access to the resources.
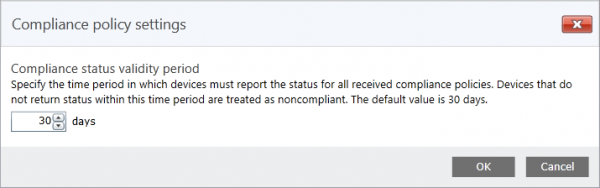
When compliant the user gets access to Exchange Online, with the compliance policy settings you are able to configure a compliance status validity period. This means that a device must report the status for all received compliance policies every XX number of days. (by default 30 days) If the device not returns a status within the period, the device will be treated as noncompliant.
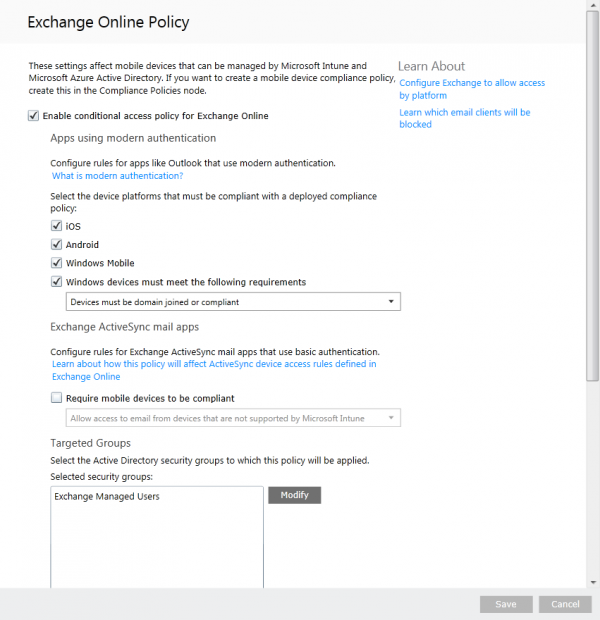
Conditional Access for Exchange Online Policy
Next we need to configure the Conditional Access of Exchange Online Policy. This is done by enabling the conditional access policy. Be sure to select the platforms you want to use and be sure that a group with users is added to the Targeted Groups.
What we don’t need to enable is the option “Require mobile devices to be compliant” in the Exchange ActiveSync mail apps section. By leaving this option unchecked the Exchange ActiveSync access rules will work.
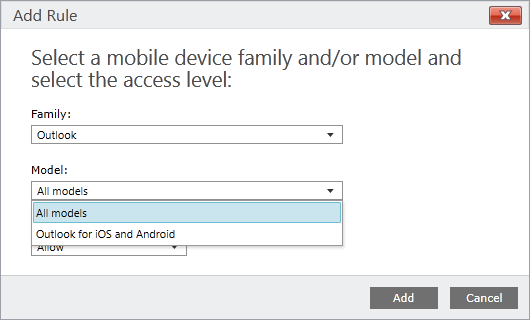
Exchange Access Rules
Under the Exchange ActiveSync node in the Policy workspace you are able to configure device access rules for Exchange ActiveSync connected devices. One of the handy things of the Outlook apps on iOS and Android is that it register itself as a device called Outlook.
So by clicking on Add Rule we are able to select Outlook as the Family and choose All Models or Outlook for iOS and Android as the model.
As a default rule Block the devices from accessing Exchange must be configured so that only Outlook has Access to Exchange Online. All Android, iOS and Windows Phone devices via the native apps will be blocked access to Exchange Online.
Show what is the result of all this?
Putting all of this together allows you to do the following;
- Have conditional access for Exchange Online via Microsoft Intune.
- Only have access via Outlook app, when enrolled into Intune.
- No access to Exchange Online via the native apps when enrolled into Intune via Exchange Access Rules.
- No access to Exchange Online via the native app when not enrolled via Exchange Access Rules.
Hope this helps, and like always test the usability for you first in a Lab environment. 🙂



Hello – Will this rule block Outlook 2013 running on a Windows 7 system from accessing email?
Hi Bob, no Outlook 2013 uses most likely Outlook Anywhere not ActiveSync.
Unfortunately when setting this up, we find that Conditional access is still overriding the Mobile device access rules and allowing the native mail client to connect.
After combing through the instructions again, and reaching out, it appears the Intune Exchange Activesync service-to-service connector was not fully established in my setup. once that was working, we were able to block the outlook client. Thanks!
great, just saw your question.. There are some issues with the service to service connector lately.. thanks for sharing!
Still works ? because I tested here and doesn’t work!
Is this also possible in a hybrid environment with SCCM?
no unfortunately not (yet)
Do you know if this works when Intune is integrated with Microsoft System Center? Your screenshots don’t look like the screens I see in the Intune portal, and I can’t get the native mail app to block emails on any mobile device platform.
I dont have the options Windows Mobile & Windows devices must meet…. in the Exchange Online Policy.
Any idea why?
you need to apply for the preview via https://connect.microsoft.com
Is using Exchange Access rule still a valid option to block the Native mail client on a iOS?
I use EXO and the service-to-service connector is setup correctly. CA is also configured and it is working but when the device is compliant I can still read email on the Native mail client if I set it up like described above. Has something changed?
Are you using stand alone or hybrid?
Standalone.
Update: I discovered that using the new Azure portal I can successfully configure CA and block the Native mail client as I wanted. So I will stick to Ibiza from now on.
Hi Alex, the new App-based CA is for MAM without enrollment only. Microsoft is still working on it for MDM+MAM..
how to block native apps on android and ios? can this be integrated with Exchange 2016 Server?
I am using standalone Intune and Native mail client will be configured automatically while enrolling device into Intune. By creating separate Conditional Access policy for iOS platform also the issue has not been fixed.
Issue: Native Mail Client is getting configured automatically while enrolling iOS device into Intune.
Need your quick assistance to rectify this issue.
Thank you in advance.